Introduction – Why Secure Remote IP Phones Matter in 2025+
Modern enterprises no longer operate from a single trusted office network. Remote offices, work-from-home agents, field staff, and temporary locations are now standard. Yet most VoIP deployments still rely on public SIP exposure, NAT traversal, port forwarding, or insecure VPN configurations.
This creates a serious problem:
VoIP systems were never designed to be safely exposed to the public internet.
That is why Secure Remote IP Phones are no longer a “nice to have” but a hard security requirement.
This blog presents a real-world, production-tested architecture using FreePBX and ZeroTier to deploy Secure Remote IP Phones in completely untrusted networks-without public SIP, without port forwarding, and without expensive SBCs.
The Core Challenge in Remote VoIP Deployments
Before designing any secure VoIP architecture, we must clearly define the problem.
Common Constraints in Real Deployments
Most remote locations suffer from one or more of the following:
- No control over firewall or router
- Shared or public LAN (hotels, hostels, shared offices)
- No public IP address
- Carrier-grade NAT (CGNAT)
- No possibility of port forwarding
- High risk of SIP scanning and toll fraud
Traditional VoIP solutions fail here.
Why Public SIP Is a Security Anti-Pattern
Exposing SIP ports (5060/5061) to the internet leads to:
- SIP brute-force attacks
- Registration hijacking
- Toll fraud
- INVITE floods
- SIP fingerprinting
- Credential harvesting
A Secure Remote IP Phones strategy must completely eliminate public SIP exposure.
Architectural Principle – Zero Trust VoIP
The foundation of this design is Zero Trust VoIP.
Zero Trust VoIP Means:
- No implicit trust based on IP address
- No public-facing SIP services
- Explicit authentication before any signaling
- Network access limited to only what is required
This is where ZeroTier VoIP fits perfectly.
Why ZeroTier for Secure Remote IP Phones
ZeroTier is not a traditional VPN. It is a software-defined, encrypted overlay network that behaves like a private Layer-2/Layer-3 switch across the internet.
Key Benefits for Secure Remote IP Phones
- End-to-end encryption (AES-256)
- NAT traversal without port forwarding
- Device-level authorization
- No exposed services
- Minimal latency for VoIP
- Easy key rotation and access revocation
Unlike traditional VPNs, ZeroTier works even on hostile or untrusted LANs.
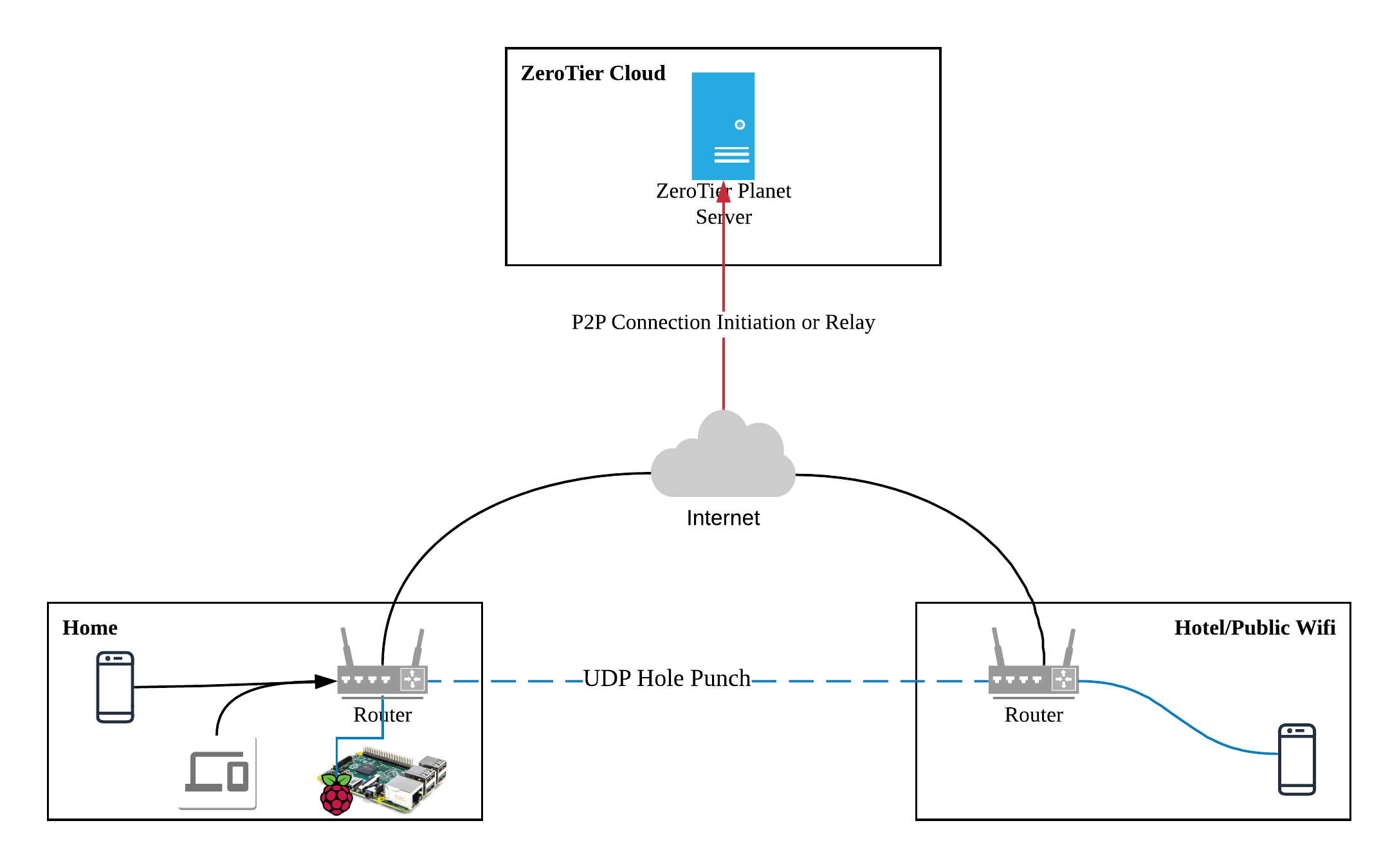
High-Level Architecture Overview
Remote IP Phone
|
| (Encrypted ZeroTier Tunnel)
|
Ubuntu ZeroTier Gateway (Restricted)
|
| (Private LAN)
|
FreePBX Server
This architecture ensures:
- The IP phone never touches the public SIP internet
- FreePBX is not reachable from the internet
- Only authorized ZeroTier members can communicate
This is the backbone of Secure Remote IP Phones.
Component Breakdown
1️⃣ FreePBX (Private Core)
FreePBX acts as the central PBX but with zero public exposure.
Hard Rules:
- No SIP ports open to the internet
- No public IP binding
- SIP listens only on private interfaces
- Access limited to ZeroTier subnet
This instantly improves Remote IP Phone Security.
2️⃣ ZeroTier Network (Encrypted Overlay)
ZeroTier creates a private virtual network across the internet.
Security Controls:
- Devices must be manually authorized
- Network rules restrict lateral movement
- Traffic is encrypted end-to-end
ZeroTier becomes the only path between the remote phone and FreePBX.
This is a core pillar of Secure VoIP Deployment.
3️⃣ Ubuntu ZeroTier Gateway (Restricted)
Instead of installing ZeroTier directly on FreePBX, an Ubuntu gateway is used.
Why?
- Blast radius reduction
- Firewall enforcement
- Device segmentation
- Easier auditing
Gateway Firewall Model
Default-deny forwarding:
- Allow SIP + RTP only
- Block SSH, HTTP, SMB, ICMP
- Phone-only access
This makes the gateway purpose-built and disposable.
4️⃣ Remote IP Phone (ZeroTier Member)
The IP phone connects via:
- ZeroTier client (if supported), or
- Routed through a small ZeroTier edge device
The phone registers to FreePBX as if it were local.
From a signaling and RTP perspective, it is local.
That is the magic of Secure Remote IP Phones.
Security Highlights Explained
✔ No Public SIP Exposure
SIP is never reachable from the internet.
This alone eliminates 90% of VoIP attacks.
✔ No Port Forwarding
No dependency on:
- NAT behavior
- ISP routers
- Misconfigured firewalls
✔ Encrypted Traffic Only
All signaling and RTP flows through ZeroTier encryption.
✔ Safe on Untrusted LANs
Even if the local LAN is compromised:
- SIP packets are encrypted
- PBX IP is hidden
- No broadcast leakage
This is enterprise-grade Zero Trust VoIP.
SIP and RTP Flow in This Design
Understanding the media path is critical.
SIP Flow
- Phone → ZeroTier → Gateway → FreePBX
- Fully encrypted
- No SIP ALG interference
RTP Flow
- Phone ↔ FreePBX directly via ZeroTier
- Stable audio
- No NAT traversal issues
This provides stable audio quality, even on hostile networks.
Why This Beats Traditional VPNs
| Traditional VPN | ZeroTier VoIP |
|---|---|
| Central tunnel bottleneck | Peer-to-peer when possible |
| Complex client config | Lightweight |
| Often exposes entire LAN | Device-level access |
| Poor NAT traversal | Excellent NAT traversal |
For Secure Remote IP Phones, ZeroTier is operationally superior.
Why SBCs Are Not Required Here
Session Border Controllers are useful when:
- Interconnecting carriers
- Handling SIP normalization
- Exposing SIP publicly
In this architecture:
- SIP is private
- Endpoints are trusted
- No protocol normalization required
Therefore, no SBC is needed.
This significantly reduces cost and complexity in Secure VoIP Deployment.
Real-World Use Cases
This architecture is ideal for:
- Call centers with remote agents
- Healthcare clinics
- Financial institutions
- Distributed enterprises
- Temporary project sites
Anywhere Secure Remote IP Phones are required.
Operational Advantages
Simplicity
- No NAT debugging
- No SIP ALG issues
- No firewall coordination with remote sites
Security
- Zero public attack surface
- Device-level revocation
- Full traffic isolation
Scalability
- Add phones in minutes
- No network redesign
- No new firewall rules
Compliance & Audit Readiness
This design supports:
- ISO 27001 principles
- Zero Trust Architecture
- Least privilege networking
- Encrypted communications
Call metadata and recordings remain protected inside the private PBX domain.
Common Mistakes to Avoid
- Installing ZeroTier directly on FreePBX without firewalling
- Allowing full LAN access over ZeroTier
- Reusing ZeroTier networks for non-VoIP traffic
- Leaving default SIP credentials
Avoiding these ensures Secure Remote IP Phones remain secure long-term.
Final Result – What This Proves
✔ Remote IP phone behaves like a local phone
✔ No public SIP
✔ No VPN headaches
✔ No SBC dependency
✔ Enterprise-grade security
This architecture proves that Secure Remote IP Phones are achievable with the right design, not expensive tools.
Final Thoughts – The Future of Secure VoIP
The future of VoIP is private by design, not exposed and defended.
Secure Remote IP Phones built on:
- FreePBX
- ZeroTier
- Zero Trust principles
represent a modern, scalable, and secure VoIP architecture.
If your current VoIP deployment still exposes SIP to the internet, the risk is not theoretical—it is guaranteed.
📌 This deployment was designed and implemented following real-world security constraints and production VoIP environments, focusing on Secure VoIP Deployment, Zero Trust VoIP, and Remote IP Phone Security.
CyberZest Tweet