Introduction
In 2026, VICIDial security is no longer optional.
A VICIDial server today is a telecom revenue engine, a regulated data processor, and a primary target for VoIP fraud groups.
At VITI Security, we are hardening VICIDial and Asterisk as a single trusted unit, assuming:
- Active toll-fraud attempts
- SIP fingerprinting
- Credential replay attacks
- Web-layer exploitation of VICIDial PHP
This blueprint focuses only on VICIDial and Asterisk hardening, with implementation-ready security controls
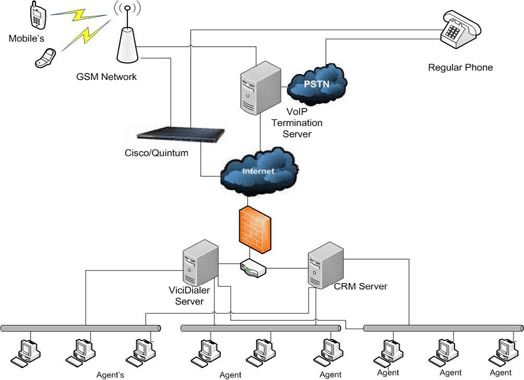
Zero-Trust Access Model for VICIDial (Without SIP Proxies)
Why IP Whitelisting Fails for VICIDial
Most VICIDial installations still rely on:
- Static IP whitelisting
- Shared admin passwords
- Flat LAN trust
This model fails in modern enterprise environments.
Zero-Trust Applied to VICIDial
Zero-Trust for VICIDial means:
- No implicit trust based on IP
- Every VICIDial login is authenticated, authorized, and logged
- Admin access is device-bound
Practical VICIDial Zero-Trust Controls
- VICIDial admin access allowed only via VPN or ZTNA
- Per-user role enforcement inside VICIDial
- No direct internet exposure of:
- /vicidial/
- /agc/
- Asterisk AMI
Zero-Trust protects VICIDial security even when credentials are leaked.
Hardening the VICIDial Web Layer (/vicidial/ and /agc/)
This is the most exploited attack surface in VICIDial.
File & Directory Hardening (Critical)
Mandatory for secure VICIDial:
- Rename:
- valid8.php
- admin.php
- Remove unused legacy scripts
- Disable directory listing
# Disable directory browsing
Options -Indexes
Renaming sensitive VICIDial files alone eliminates 90% of automated attacks.
Enforce Phishing-Resistant MFA for VICIDial Admins
Passwords + OTP are no longer secure.
Required Controls
- Hardware-backed MFA (FIDO2 / Passkeys)
- No SMS or email fallback
- Enforced for:
- VICIDial admins
- VICIDial managers
Supervisor roles
This directly improves VICIDial security posture.
Web Application Firewall for VICIDial
A WAF is mandatory for enterprise VICIDial.
Protect Against
- SQL Injection in VICIDial PHP
- XSS via agent forms
- Brute-force login attempts
- Automated scanner traffic
# Block SQL injection attempts
if ($query_string ~* "(union.*select|sleep\(|benchmark\()") {
return 403;
}
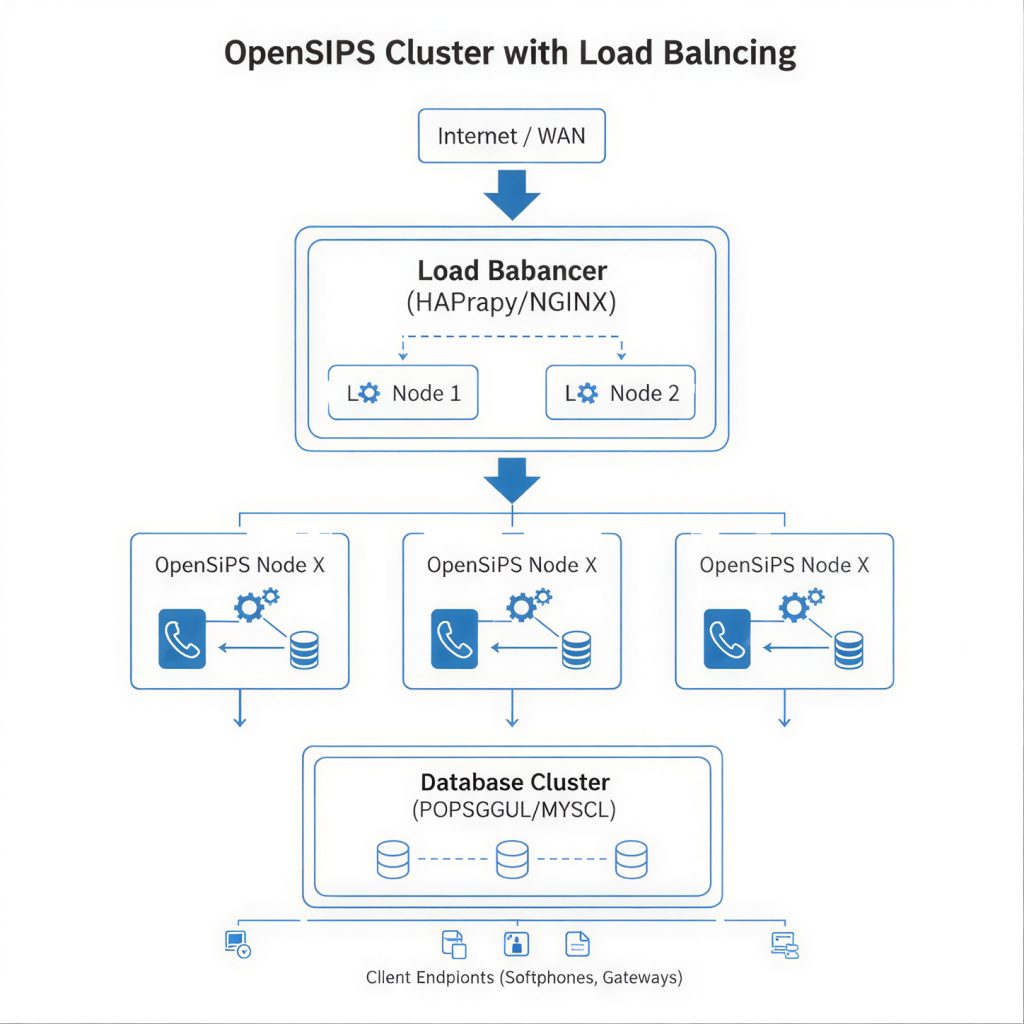
Asterisk SIP & VoIP Fraud Mitigation (VICIDial Core)
This is where real money is lost.
SIP Authentication Abuse Protection
Attackers exploit:
- 401 / 407 challenges
- Weak SIP authentication retry logic
Hardening Asterisk
# Limit authentication attempts
auth_limit=5
auth_timeout=30
- Drop repeated failures
- Enforce strong digest auth
- Reject malformed SIP headers
SIP INVITE Rate Limiting (Mandatory)
Unrestricted INVITEs = toll fraud.
# Rate-limit SIP traffic
iptables -A INPUT -p udp --dport 5060 -m hashlimit \
--hashlimit-name sip --hashlimit 10/sec --hashlimit-burst 20 -j ACCEPT
This directly protects VICIDial from fraud attacks.
Call Pattern Anomaly Detection
Monitor:- Sudden international dialing
- Out-of-hours traffic spikes
-
High ASR with low billable seconds
Automated response:
- Drop calls
- Disable trunk
- Alert SOC
This is real-time VICIDial fraud prevention.
Database Hardening for VICIDial
MySQL / MariaDB Security
VICIDial databases are high-value targets.
# Disable file-based exploitation
SET GLOBAL local_infile = 0;
Additional controls:
- Remove FILE privilege
- Enforce TLS
- Separate DB users for VICIDial services
Secure Call Recordings Storage
Call recordings = regulated data.- Dedicated partition
- Disk-level encryption
- Restricted permissions
chmod 700 /var/spool/asterisk/monitor
This protects VICIDial call recordings from insider abuse.
The 2026 Threat Landscape for VICIDial
AI-Generated Voice Fraud
Attackers now:
- Clone agent voices
- Fake supervisor calls
- Bypass verbal verification
Mitigation
- No voice-only authentication
- Call-back verification
- Context-based approval flows
Automated SIP Scanners & Botnets
Modern botnets:
- Fingerprint Asterisk behavior
- Adapt INVITE patterns
- Evade static firewalls
Defense:
- SIP rate limiting
- Behavioral monitoring
- Continuous log analysis
VITI Security – VICIDial Hardening Checklist (2026)
VICIDial Web Security
- ☑️Renamed sensitive PHP files
- ☑️WAF enabled
- ☑️FIDO2 MFA enforced
Asterisk Security
- ☑️ SIP rate limiting
- ☑️Auth abuse detection
- ☑️Trunk anomaly monitoring
Database & OS
- ☑️LOAD_FILE disabled
- ☑️Encrypted recordings
- ☑️Strict permissions
Governance
- ☑️Full audit logs
- ☑️SOC alerting
- ☑️Incident response playbooks
Final Word (Very Important) VICIDial security is not about adding more components. It’s about hardening what already exists — correctly.
CyberZest Tweet